Week2_My_GBC
Week2_My_GBC
分析
安全策略

逆向分析
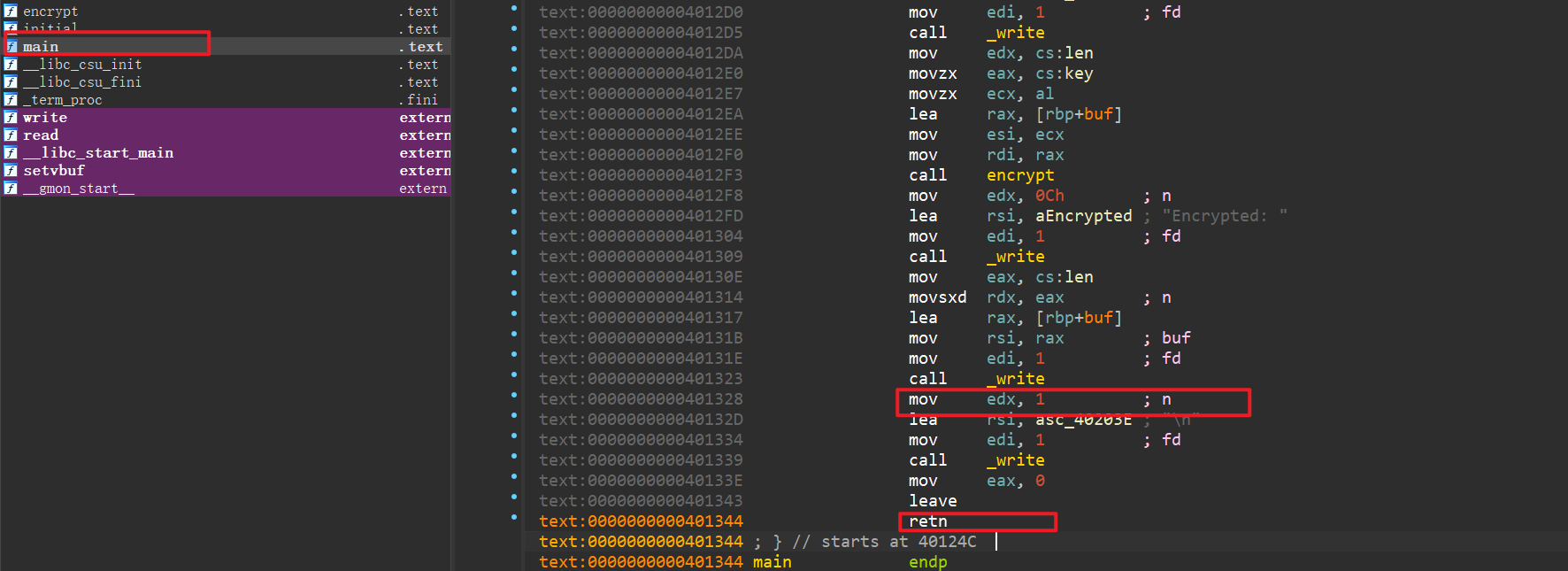
写入buf,输入buf,通过key对buf内容加密,输出加密后的buf,return 0,写入payload会被加密干扰


- 对buf的内容的每位字节依次异或a2,然后循环左移3位
_BYTE:一种类型定义(通常为unsigned char或char),表示该操作是针对 1 字节数据- 逻辑(无符号数)左移:SHL,右移:SHR
- 算术(有符号数)左移:SAL,右移:SAR
- 循环左移:ROL,右移:ROR

- 只需要payload循环右移3位然后依次异或a2,即可保持原payload执行
exp
注不是所有的C3都可以作为ret,只有位于代码段(通常位于.text段里面),这就是不能用的
利用csu的泄露libc地址
1 | |
参考
官方wp
看完wp1后,才看懂官方,感觉官方的比较复杂
第一步使用csu泄露read地址
第二步使用csu,将payload1写入内存地址
第三步使用csu,对齐栈,为了执行payload1中的syscall先
- 使用payload1的一个栈帧跳过call的返回地址
第四步使用csu执行内存地址的
execve('/bin/sh\x00',0,0)
My_GBC!!!!! | WriteUp - NewStar CTF 2024
构造 ROP 链利用 CSU 初始化序列
1 | |
ret可以放到最后的csu_2前面,都是为了栈对齐
不能放在第二步的后面,由于需要7个参数来间隔返回地址,放在后面会被add rsp,8影响,这样的
官方是通过add rsp,8;ret才能放在最后的
wp1——通过ret2csu调用write泄露read地址
最容易想懂的一个wp
[NewStarCTF 2024 | Bosh’s Blog](https://z-bosh.github.io/2024/10/20/NewStarCTF 2024/)
1 | |
call[r15+rbx*8]不需要手动在栈中添加返回地址,call会自己将返回地址压入栈中,只需要7个栈帧用来抵消add rsp,8与pop指令
wp2——利用已有资源泄露libc
[NewStar 2024] week2_newstar2024 week2-CSDN博客
每次只能泄露1字节(由于rdx等于1,且没pop rdx),泄露完libc就可以直接getshell

1 | |
- 使用r15只是由于rsi与r15绑定了,随便给r15赋个值
ret2csu学习
Week2_My_GBC
http://sh1j1.github.io/2024/11/25/Week2-My-GBC/